
Asymmetric Cyber Warfare: Protect Your Business from Sneaky Attacks
 Read Time: 7 minutes
Read Time: 7 minutesSocial engineering is becoming one of the most effective ways to steal data because it targets people, not systems. This kind of indirect cyber attack is part of a growing trend of asymmetric threats—but the right systems and protocols can protect both your team and your business.
If you’ve heard about Qantas Airlines recently, it probably wasn’t in a good way. Earlier this year, hackers stole the personal data of 5.7 million Qantas customers. Actually, the airline wasn’t the direct target—their third-party offshore call center was. And this brings us to a concept all business owners should know: Asymmetric Cyber Warfare.
What Is Asymmetric Cyber Warfare?
Asymmetric warfare is used by weaker forces against stronger ones by targeting vulnerable points like communication networks, contractors, or—you guessed it—third-party suppliers. It’s more successful than engaging in direct confrontation because it takes advantage of weak links that can be found outside of normal defenses.
Make no mistake: if you own a business, you are at war. Data is currency, and modern business operations are digitally integrated with so many systems, vendors, SaaS, and service providers that the potential for weak links is everywhere. This means cybersecurity is no longer just an IT job. Every team, from customer support to finance, touches data or systems that need protection.
So let's take a look at four common cybersecurity threats that attack in indirect ways, and what you can do to shore up your defenses against them.
Vishing
A new(ish) twist on an old favorite, “vishing” is voice phishing, and it’s what catapulted Qantas into their current quandary. Qantas’ offshore call center was contacted by a threat actor over the phone. This person used social engineering to convince the representative to give them access to a third-party platform full of sensitive customer data. From there, it was only a matter of days before Qantas was contacted by the threat actors, likely in an attempt to extort the company to prevent the release of the stolen data.
Vishing can happen over the phone, through business apps like Teams or Zoom, and can even involve AI-generated voice to convince someone that they are talking to a trusted figure. The goal is to extract login credentials or bypass multi-factor authentication (MFA). Humans are the entry point, so any third-party vendor with access to your data that has lower security training, protocols, or standards can be a backdoor into your system.

Protect Yourself from Voice-Based Scams
- Train your staff to be suspicious of pressure tactics. If someone is pressuring a team member to act quickly, especially over the phone, that’s a red flag. Confirm unusual requests through a separate, trusted channel, like calling the person back on a known number. Build a culture where it’s okay to slow down and double-check.
- Stick to trusted platforms. Whenever possible, work with vendors who already have a solid reputation or are widely used in your industry.
- Check for MFA and role-based access. Before giving any vendor access to your systems, make sure they support multi-factor authentication (MFA) and that you can limit what they see or do based on role.
- Keep a record of your vendors and review it once a year. Remove access that’s no longer needed.
- Bring in help before you need it. Hiring a consultant or Fractional CTO to vet third-party vendors can help bridge gaps that would otherwise leave your team feeling overwhelmed.
Third-Party App Impersonation
Attackers often create spoof versions of widely used business tools and email links to people, hoping that recipients will log in to the fake site with their very real credentials. Those credentials are harvested and used to gain access to employee accounts and sensitive data.
For example, recent months have shown a spike in phishing campaigns abusing the DocuSign brand. Attackers are sending fake DocuSign “envelope” emails that look nearly identical to the real thing, prompting recipients to click links like “review document” or to open attachments. Some campaigns even include QR codes intended to direct victims to credential-harvesting sites when scanned. This tactic is called “quishing” and is often successful because mobile devices may lack enterprise-grade security controls.
Shut Down Fake Apps and Spoofed Links
- Pause before clicking. Train your team to hover over links and inspect URLs before taking action. If something seems off, verify through a trusted channel.
- Use a password manager. These tools won’t autofill credentials on spoofed websites; if the site is fake, the manager won’t recognize it.
- Block QR codes in emails. Where possible, filter or flag messages containing QR codes, especially from external senders.
- Enable login alerts. Turn on notifications for logins from new locations or devices to catch compromised credentials early.

Business Communication Hijacking
Internal communications platforms like Slack and Zoom start to feel safe to team members who live in them every day. Within these apps, colleagues help each other put out fires, share crucial information, and even let their hair down with a meme now and then (or in our case, all day every day). Unfortunately, the high-trust environments these platforms promote are no longer as insulated as they may seem.
Last year, threat actors exploited the trust people place in Microsoft Teams to slip past defenses across multiple industries. They masqueraded as real employees by using disguised accounts and sent malware to unsuspecting colleagues. Adjusting their tactics in real time based on their target’s responses, they embedded malicious files in what appeared to be normal chats.
In situations like these, victims don’t think to question attackers because the requests for access, file sharing, and financial transfers all come and go through a space that feels like home.
Train your employees to understand that just because something comes from an internal tool, it is not automatically safe.
This is why companies need to adopt the motto of defensive basketball great Dikembe Mutombo on internal communications: “Not in my house!” Employees should be trained to block attackers’ shots like “Mount Mutombo” himself.

Defend Against Internal Chat Impersonators
- Don’t leave the doors open on anything that connects your team. MFA must be mandatory on everything.
- Control entry, not just behavior. Require explicit admin approval for every new account, whether it's a contractor, vendor, or new hire. Don’t allow open or auto-approved invitations to your internal communication tools.
- Train your team to double-check out-of-character behavior. When the word “urgent” appears, or if a message encourages haste, deliberately slow the pace and investigate.
Phishing, Smishing, and BEC
In 2024 alone, the FBI reported over $2.77 billion in Business Email Compromise (BEC) related losses, and small to mid-sized businesses were among the most frequent targets. BEC is a targeted scam where attackers impersonate someone the victim trusts, often a company executive or coworker, in order to trick employees into transferring money, sharing sensitive data, or granting system access. Scammers often do research first (like checking LinkedIn for employee names, press releases for organizational details, and websites for email address formats) so they can craft believable, targeted messages like these:
- “Can you send me the client list before our meeting?”
- “Please process this urgent wire transfer by EOD.”
- “We’ve changed our banking details. Use the new account below.”
The displayed name might match the CEO or colleague, but it’s often from a slightly altered (or wildly different) domain. My employees receive emails from “Jamie Smyth” at an array of different domains, and of course none of them are from me.
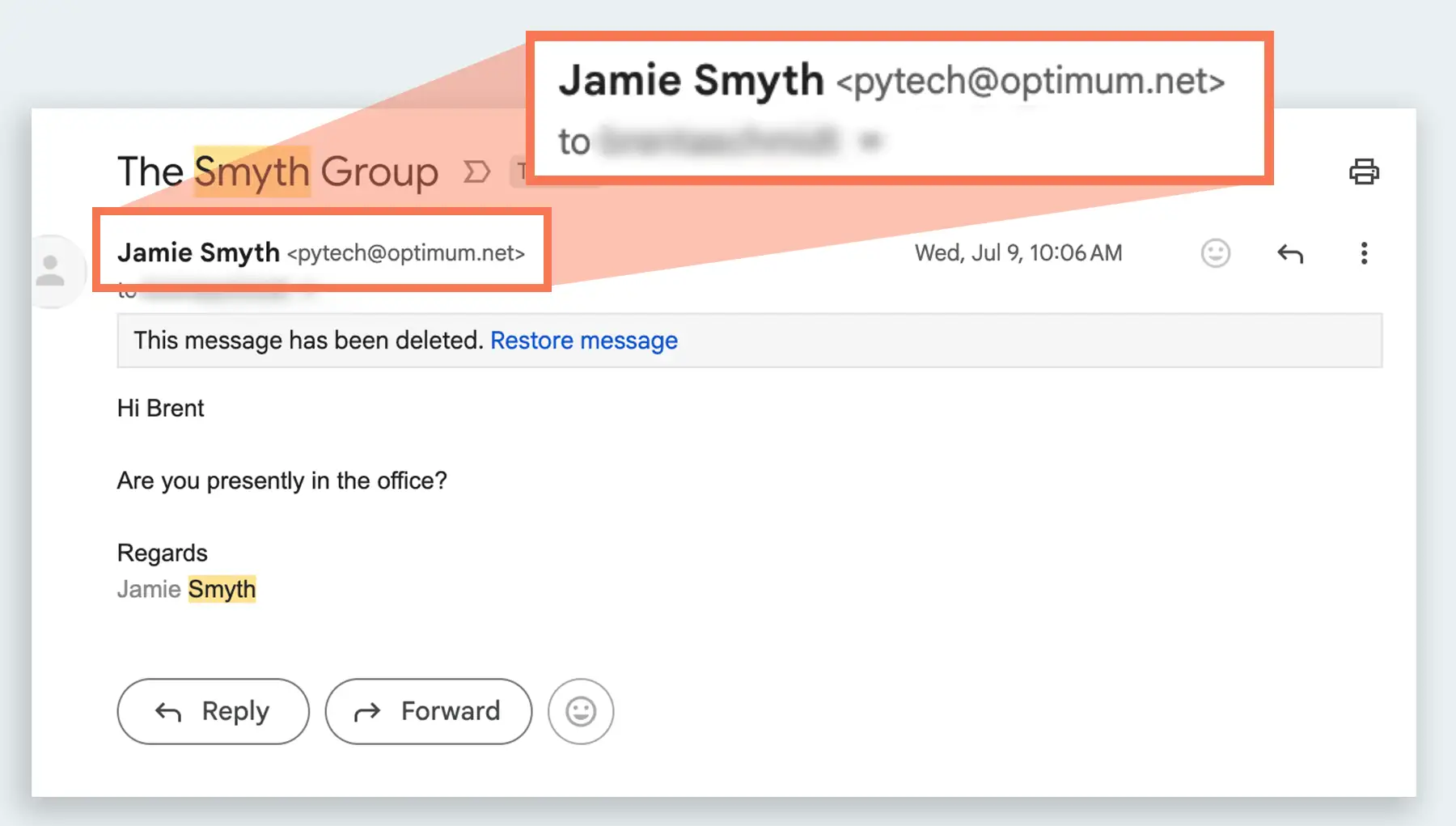
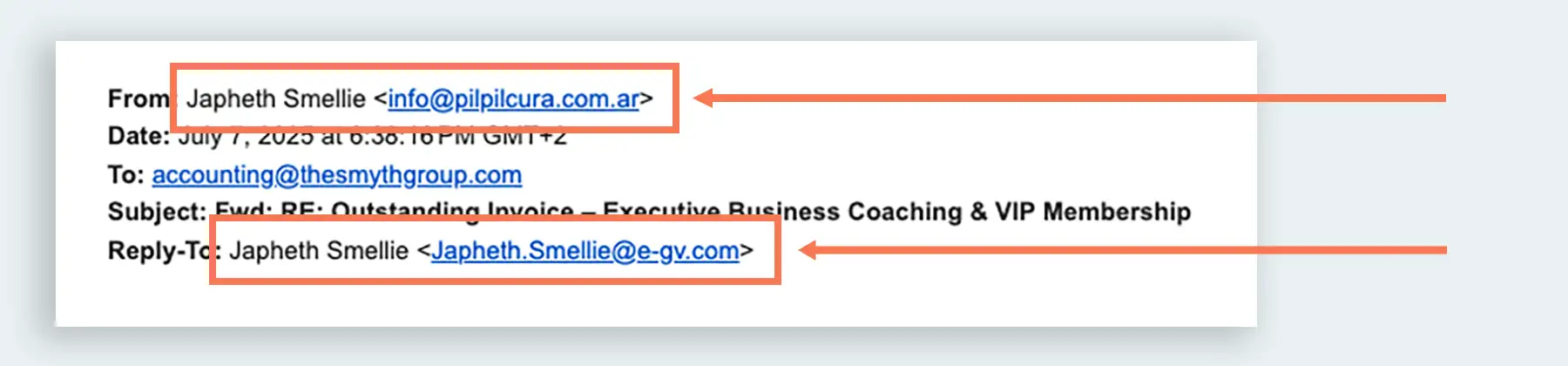
Recently, our accounting department received an email that appeared to be forwarded from our COO Japheth requesting payment of an invoice. This phishing attempt was more sophisticated than usual in that it included a thread of emails that appeared to be Japheth discussing the invoice with a vendor and approving the payment. I use the term “sophisticated” loosely because the fake Japheth had not one but two outlandish email addresses recorded in the chain.
Attackers have recently impersonated our company in smishing scams (phishing via SMS or text), even setting up fake websites using ripped-off versions of our logo.
Spot and Stop Email and Text-Based Scams
- Train your team to slow down. I realize I’m starting to sound like a broken record, but phishing and BEC scams rely on urgency. Teach your employees that it’s okay (and expected) to double-check unusual requests, especially anything involving money, sensitive data, or credentials.
- Verify domains, not just names. Email display names are easy to spoof. Encourage your staff to be suspicious and check the full sender address.
- Set up email rules and warnings. Use tools that flag external emails, alert users to domain mismatches, or tag messages that might be impersonating internal contacts.
- Report and escalate. Make it easy for employees to report suspicious messages. Every flagged email is a chance to tighten filters and prevent the next one. We turn it into a bit of a game, where employees joke about being “left out” if they haven’t been a target.

Harden the Weakest Links
Today’s cyberattacks are Asymmetric Warfare—calculated strikes aimed not at your strongest defenses, but at your overlooked weaknesses. Successful defense can be found in awareness, training, and careful management of third-party access. Create a culture where it’s safe for people to slow down and ask questions. When employees learn to recognize social engineering and suspicious activity, they become your first line of defense instead of your greatest risk. Using role-based access, MFA, and regularly reviewing vendor permissions will protect you if you’re the target of an attack.
With these basic protections, thoughtful habits, and a culture that values skepticism over speed, your business can stay resilient even when the attacks come from unexpected angles.

We are custom software experts that solve.
From growth-stage startups to large corporations, our talented team of experts create lasting results for even the toughest business problems by identifying root issues and strategizing practical solutions. We don’t just build—we build the optimal solution.
From growth-stage startups to large corporations, our talented team of experts create lasting results for even the toughest business problems by identifying root issues and strategizing practical solutions. We don’t just build—we build the optimal solution.


